Wireshark 101
Wireshark is tool used for creating and analyzing PCAPs(network packet capture files).
Wireshark uses OSI layers to break down packets.
7 Layers of the OSI Model
Application - End User layer
- HTTP, FTP, IRC, SSH, DNS
Presentation - Syntax layer
- SSL, SSH, IMAP, FTP, MPEG, JPEG
Session - Synch & send to port
- API's, Sockets, WinSock
Transport - End-to-end connections
- TCP, UDP
Network - Packets
- IP, ICMP, IPSec, IGMP
Data Link - Frames
- Ethernet, PPP, Switch, Bridge
Physical - Physical structure
- Coax, Fiber, Wireless, Hubs, Repeaters
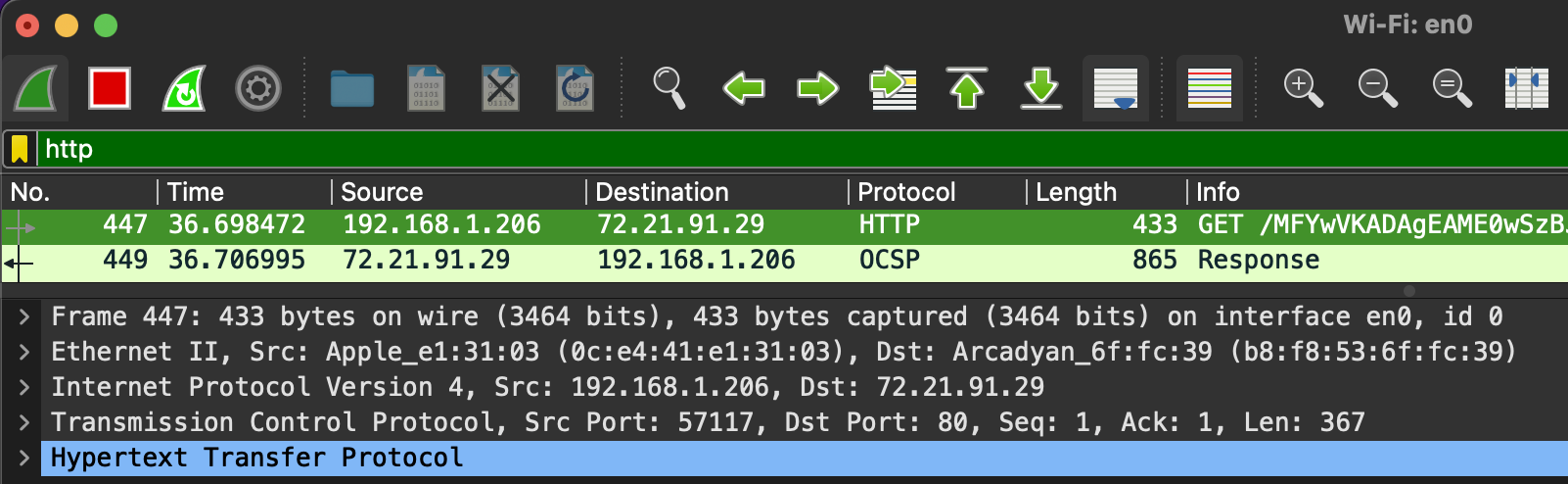
Packet Details (e.g. HTTP)
- Frame (Physical layer): show you what frame / packet you are looking at.
- Source [MAC] (Data Link layer): show you the source and destination MAC Addresses.
- Source [IP] (Network layer): show you the source and destination IPv4 Addresses.
- Protocol (Transport layer): show you details of the protocol used (UDP/TCP) along with source and destination ports.
- Protocol Errors (not showing in the pic): show specific segments that needed to be reassembled.
- Application Protocol (Application layer): show details specific to the protocol being used.
- Application Data (not showing in the pic)
ARP
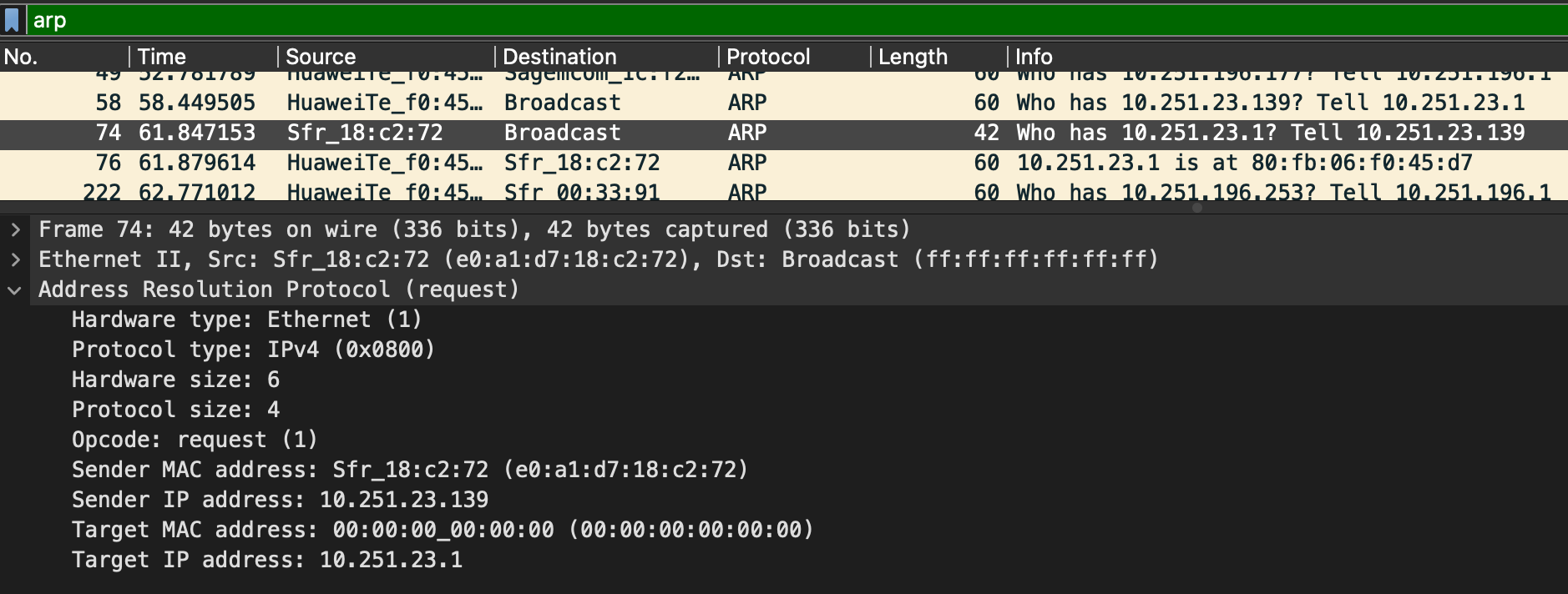
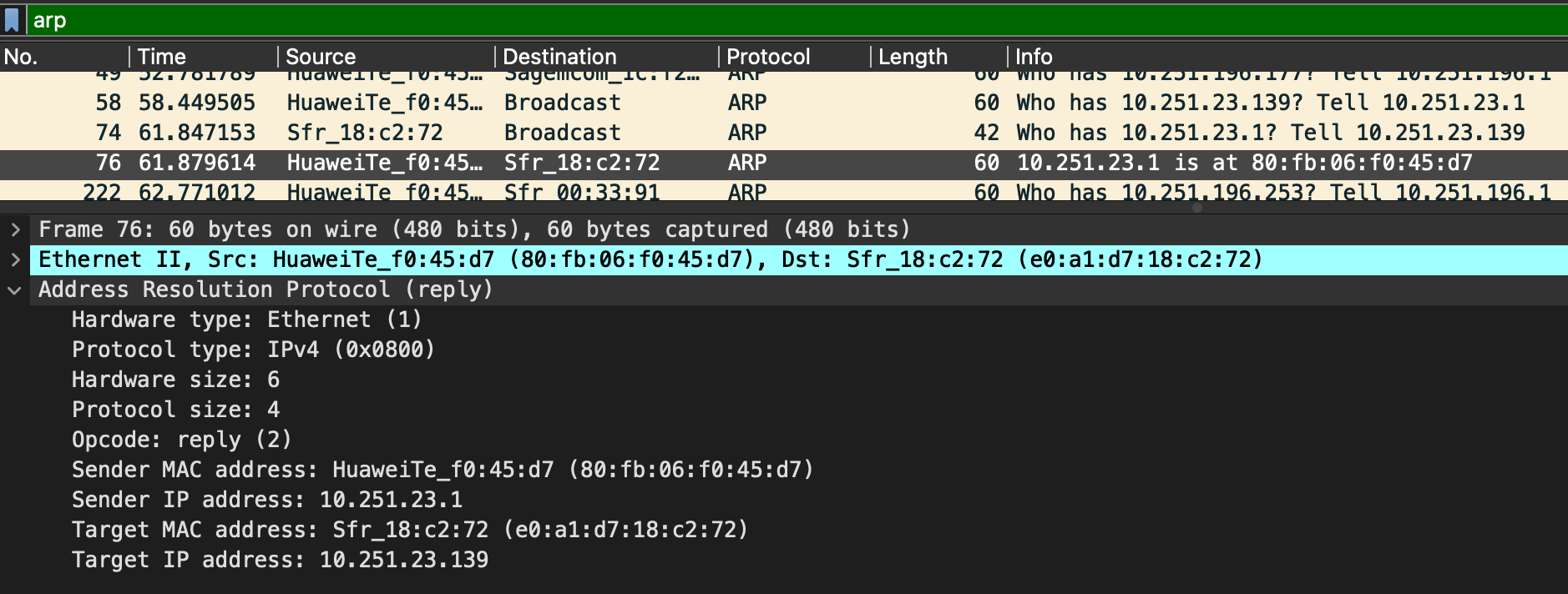
ARP(Address Resolution Protocol) is a Layer 2 protocol that is used to connect IP Addresses with MAC Addresses. They will contain two type of messages(operation codes):
- Request(1)
- Reply(2)
ARP Request
ARP Reply
ps: filter by mac address
eth.src == [mac address]
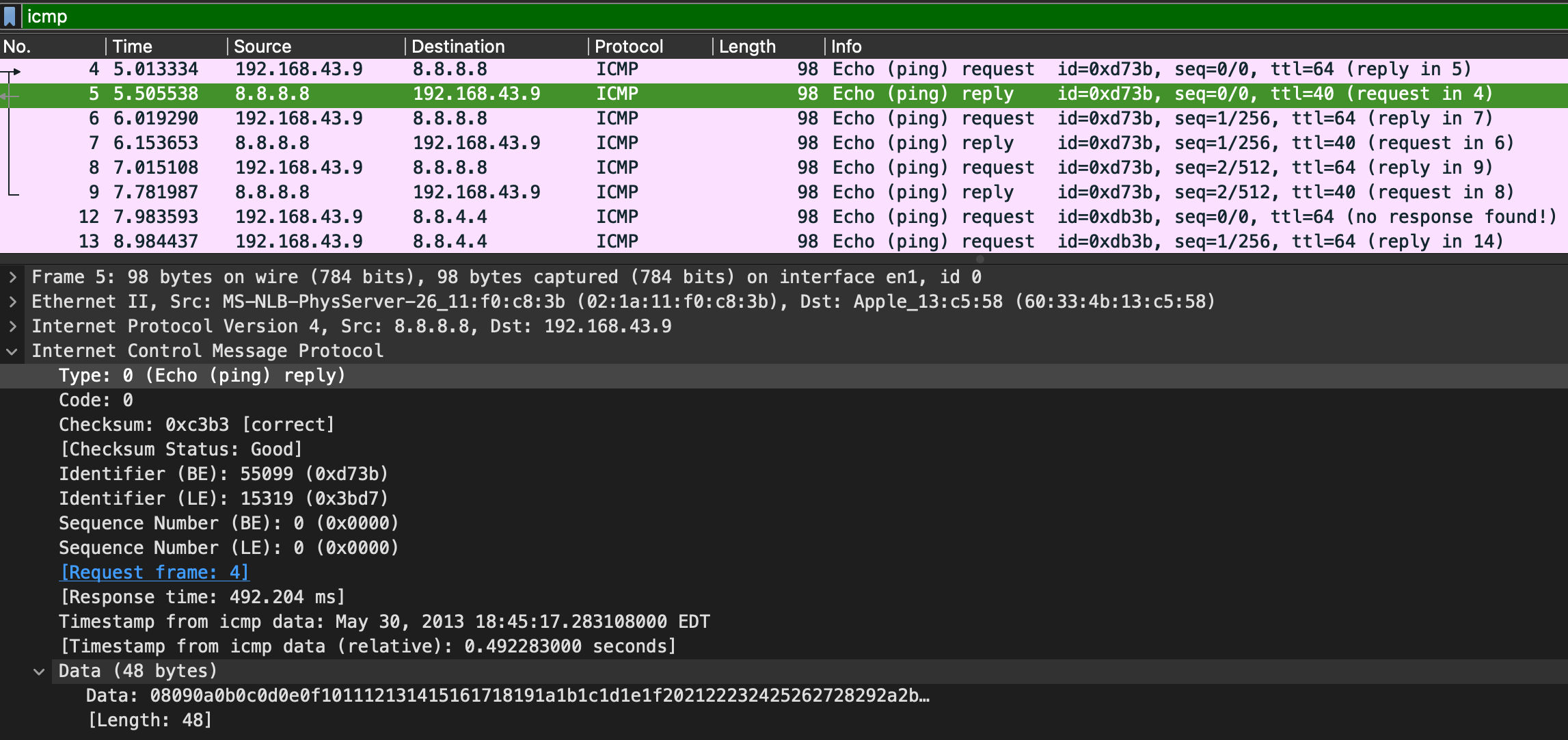
ICMP
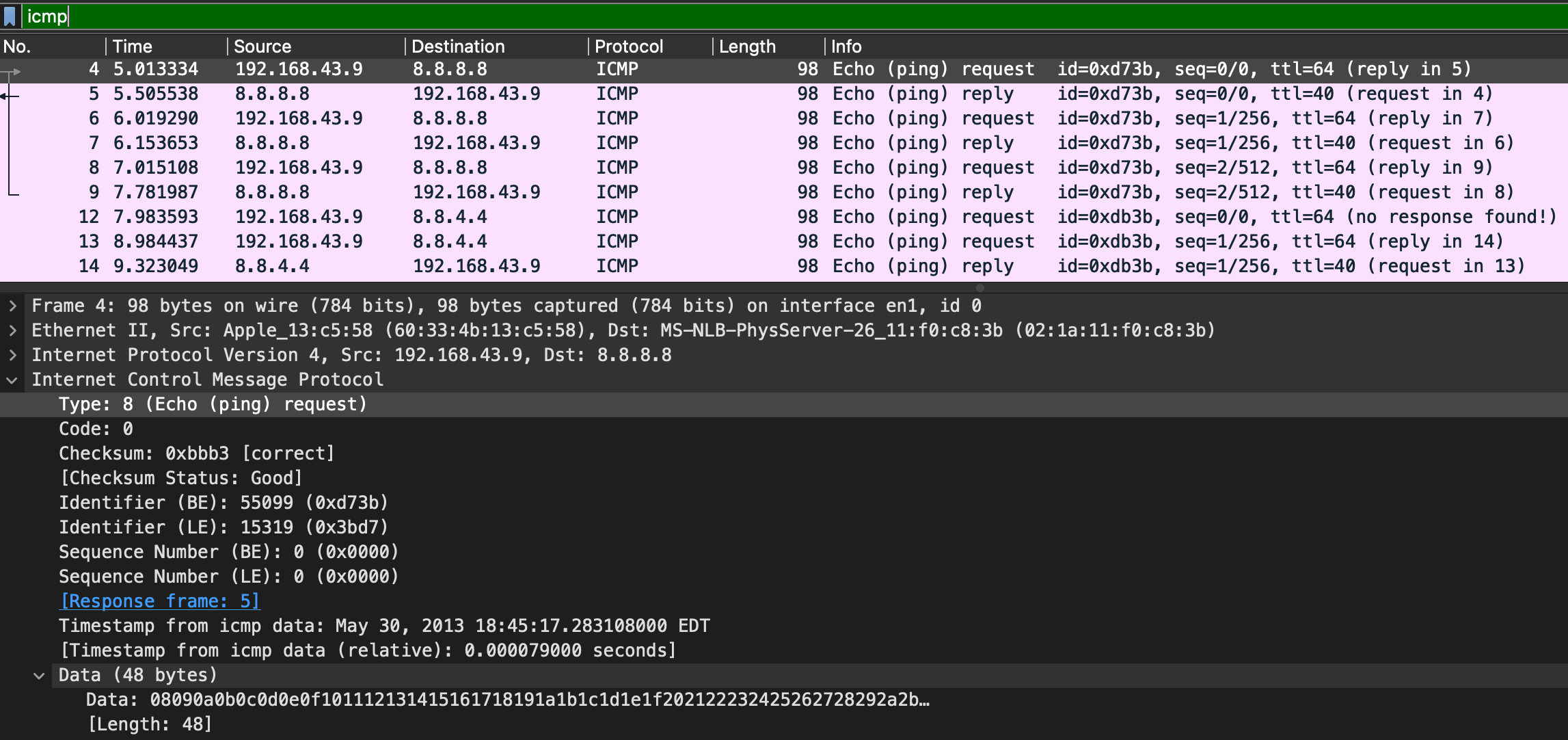
ICMP(Internet Control Message Protocol) is used analyze various nodes on a network. A ping would have a request and a reply.
Packet details:
- type
- 8: means that it is a request packet
- 0: means that it is a reply packet
- code
- do not seem correct: a sign of suspicious activity
- timestamp
- identify the time the ping and suspicious activity in some cases.
- data
- typically just be a random data string
ICMP Request
ICMP Reply
TCP
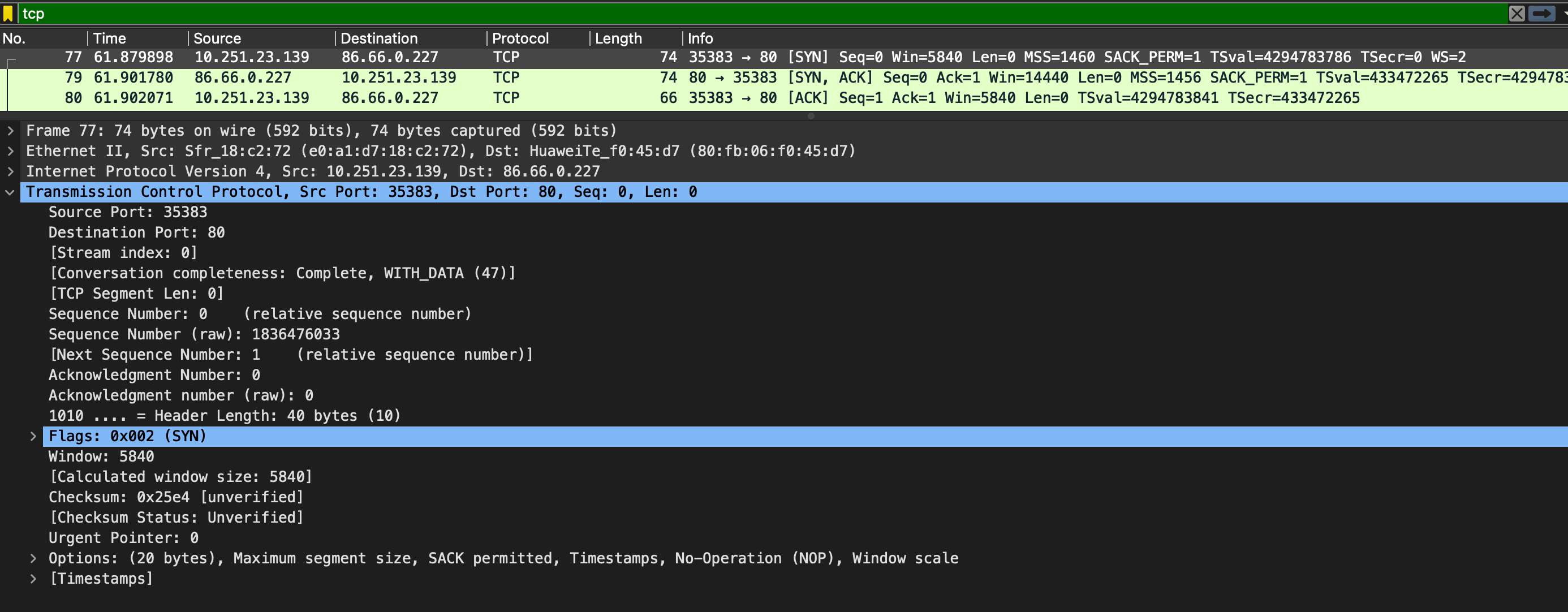
TCP(Transmission Control Protocol) handles the delivery of packets including sequencing and errors.
TCP handshake:
- syn
- syn, ack
- ack
Packet Analysis
- sequence number
- acknowledgment number
DNS
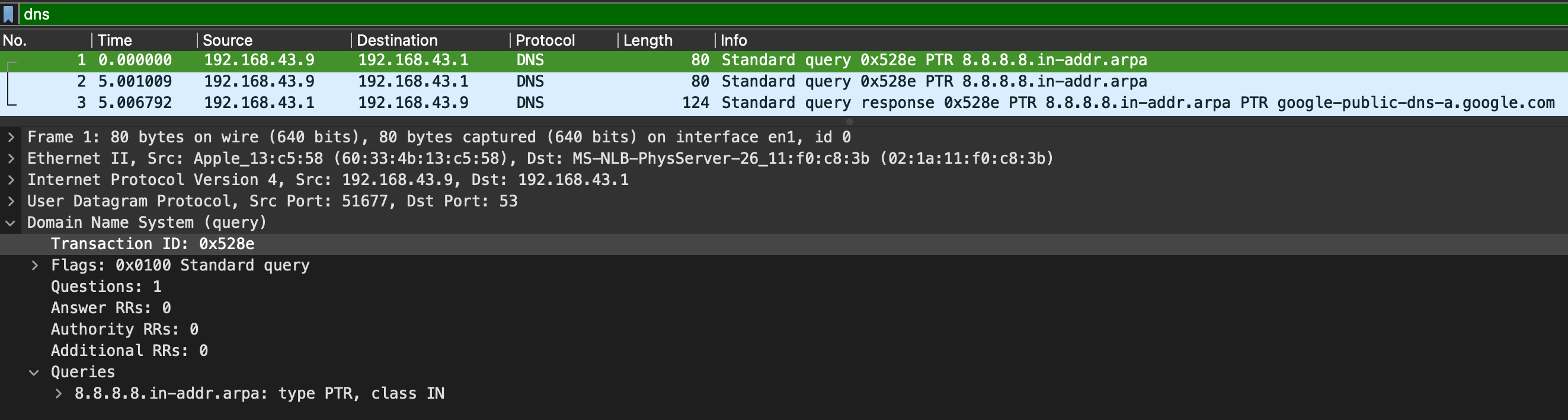
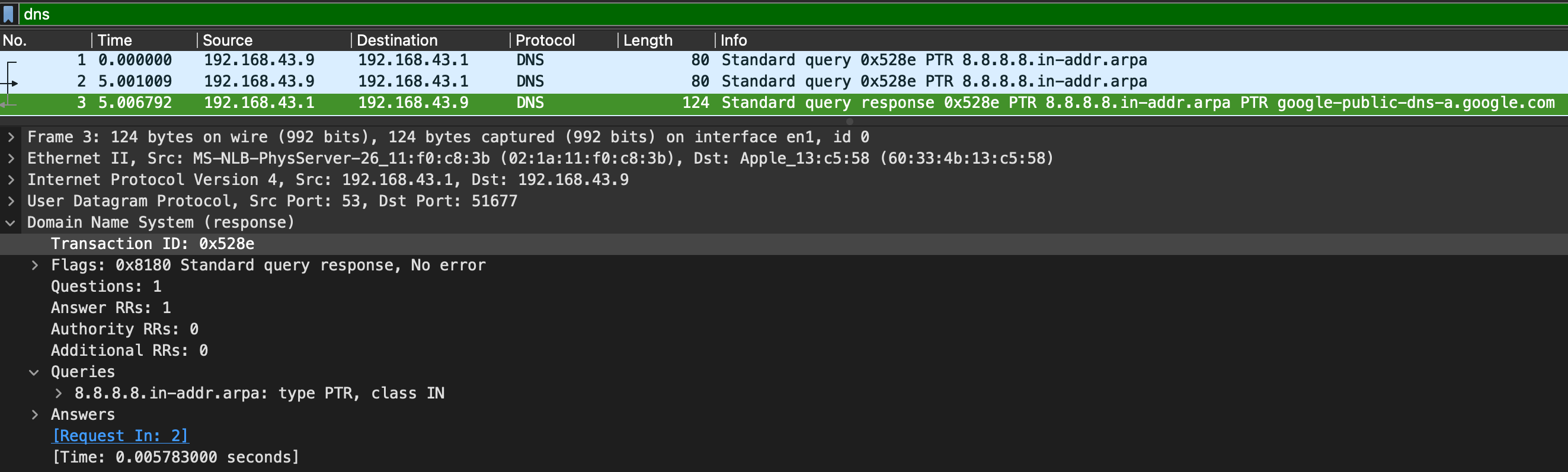
DNS(Domain Name Service) is used to resolves names with IP addresses.
Packet Analysis:
- Query-Response
- DNS-Servers Only
- UDP: the query should originated from UDP 53. If it was TCP 53 then it should be considered suspicious traffic.
DNS Query
DNS Response
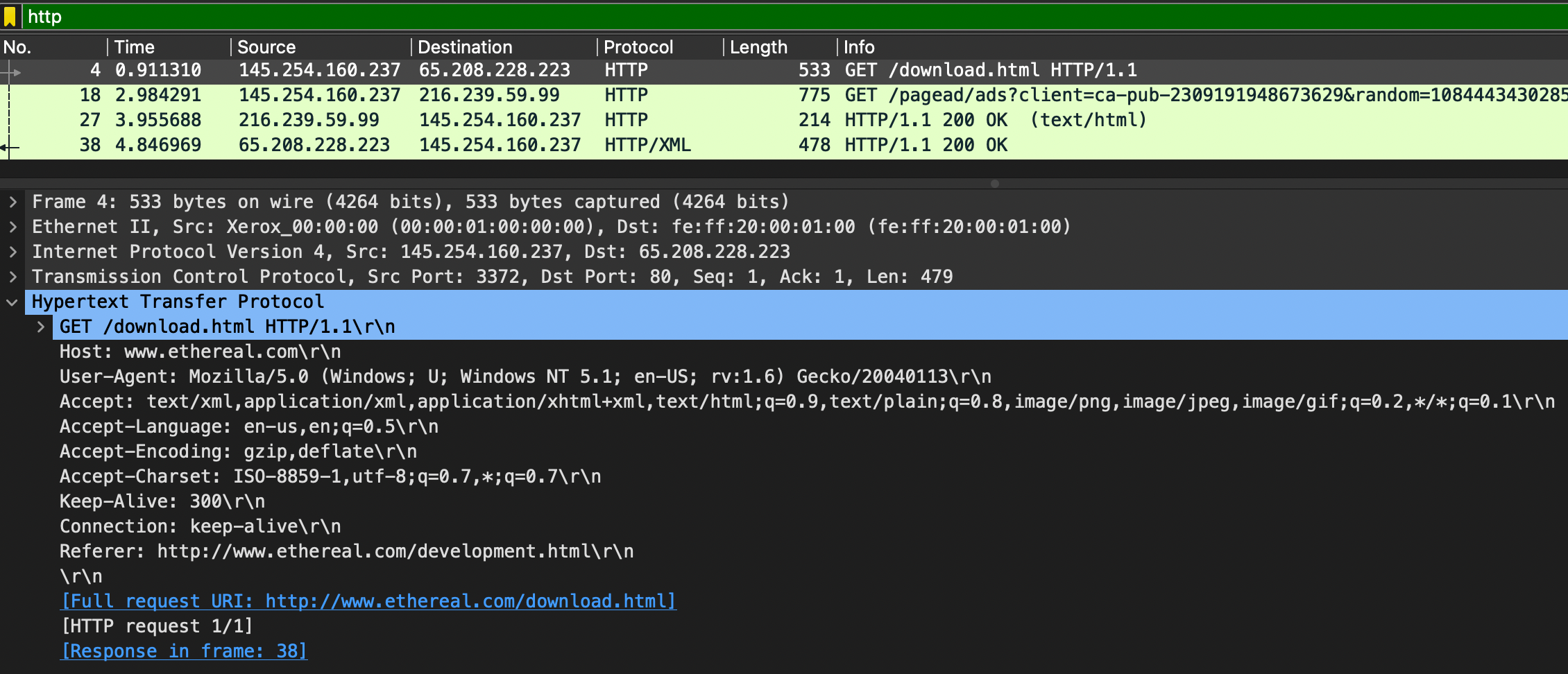
HTTP
HTTP(Hypertext transfer Protocol) is a commonly used protocol for the world wide web and used by some websites. It is used to send GET and POST requests to a web server in order to receive things like webpages.
Packet Analysis
- Very straight forward. No handshakes or prerequisites before communication.
HTTP request
- host
- user-agent
- requested URI
- response
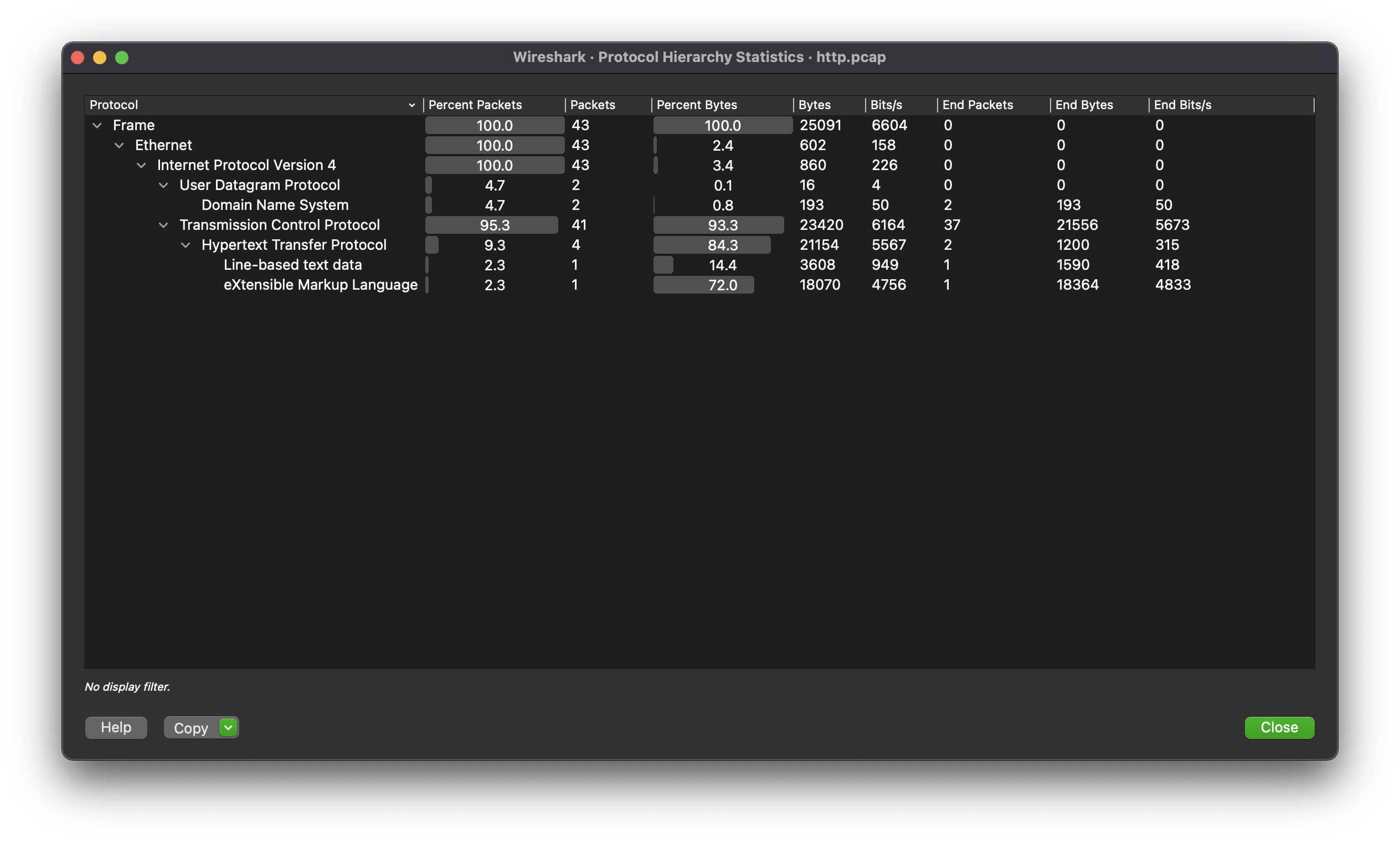
Some useful features:
Statics > Protocol Hierarchy: can be very useful in practical applications like threat hunting to identify discrepancies in packet captures.
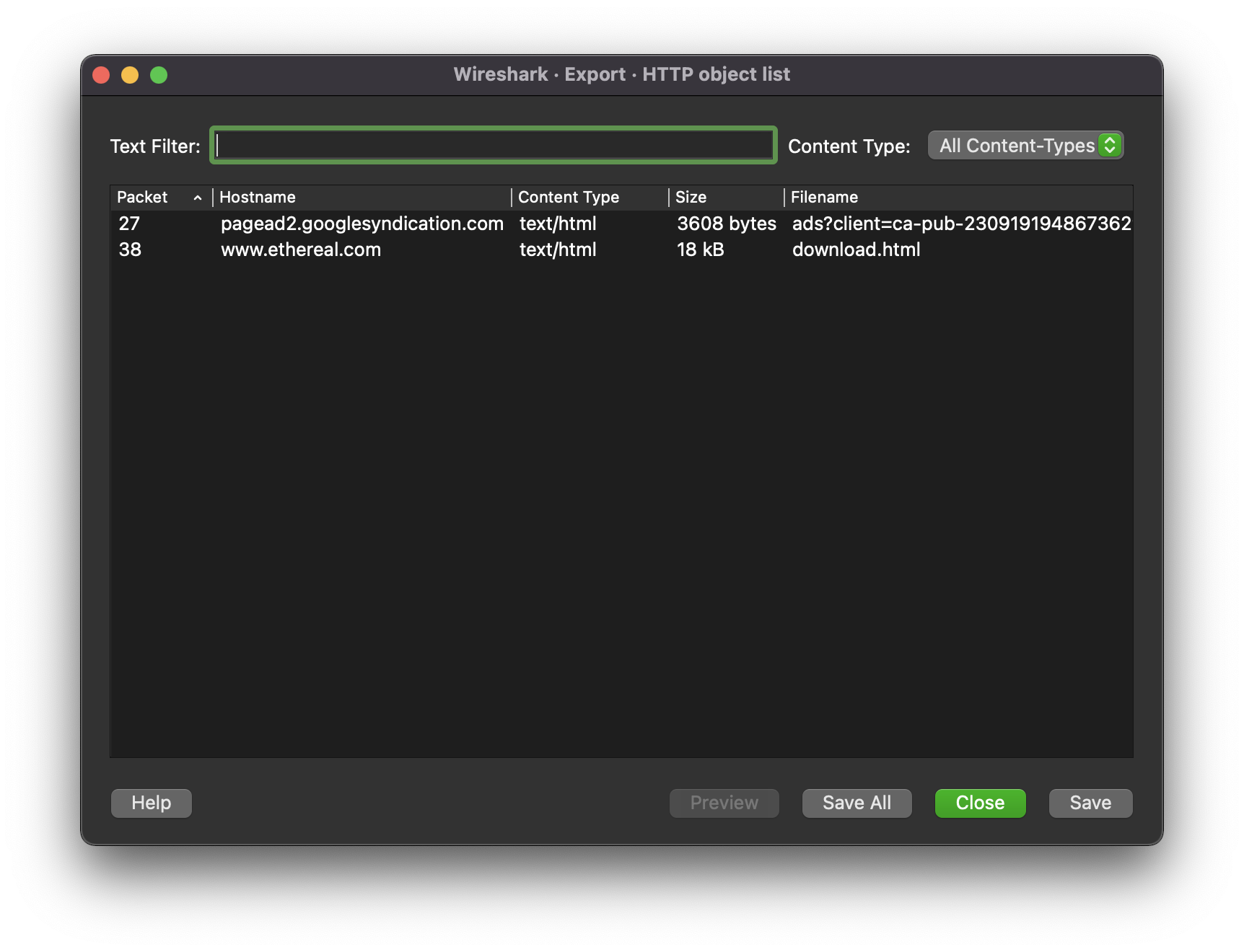
file > Export Objects > HTTP: can be useful to quickly identify possible discrepancies in captures.
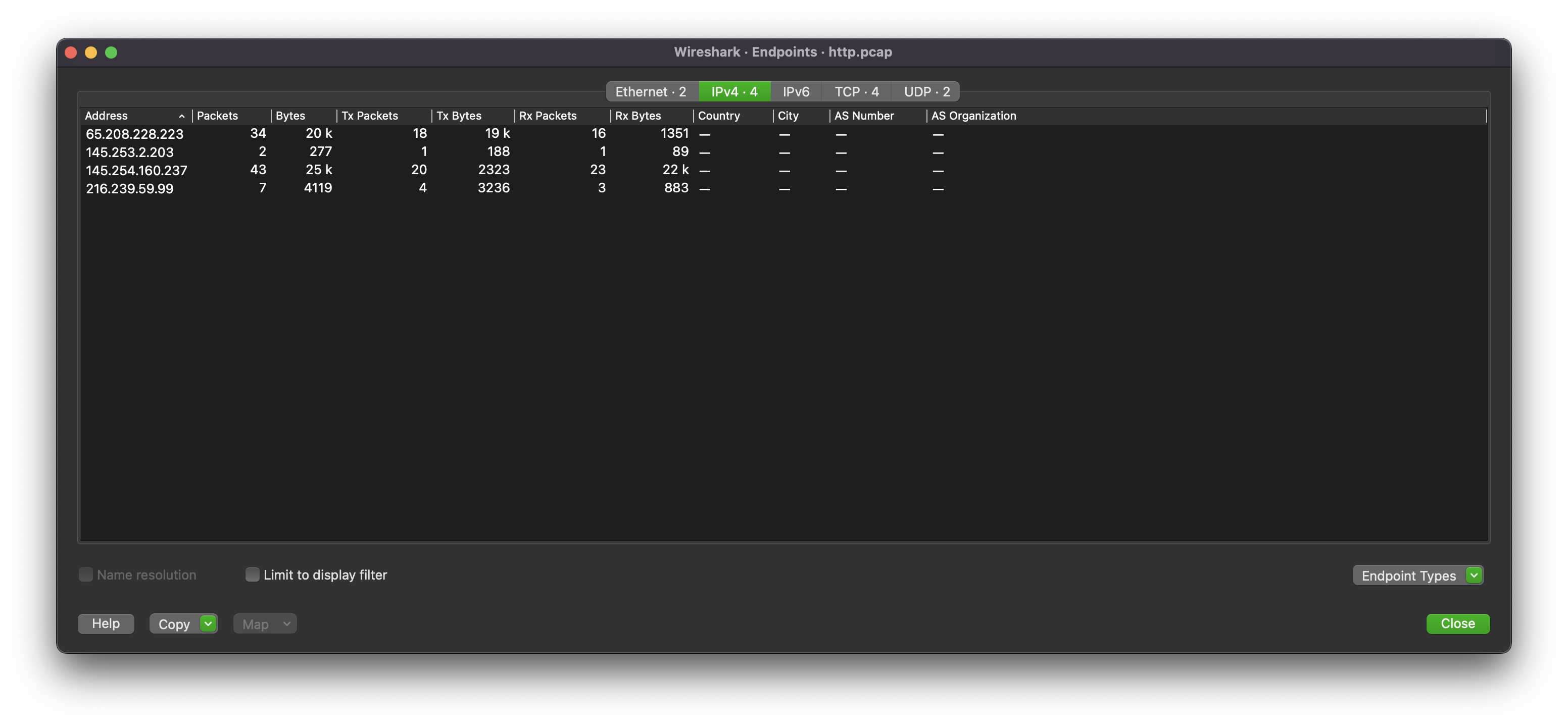
Statics > Endpoints: allows the user to organize all endpoints and IPs found within a specific capture. Can be useful to identify where a discrepancy is originating from.
HTTPS
HTTPS(Hypertext Transfer Protocol Secure) can be annoying to understand from a packet analysis perspective.
Before sending encrypted information the client and server need to agree upon various steps in order to make a secure tunnel.
- Client and server agree on a protocol version
- Client and server select a cryptographic algorithm
- The client and server can authenticate to each other
- Creates a secure tunnel with a public key
Packet Analysis
All of the requests are encrypted. We can use an RSA key to view the data unencrypted.
Preferences > Protocols > TLS > [+]
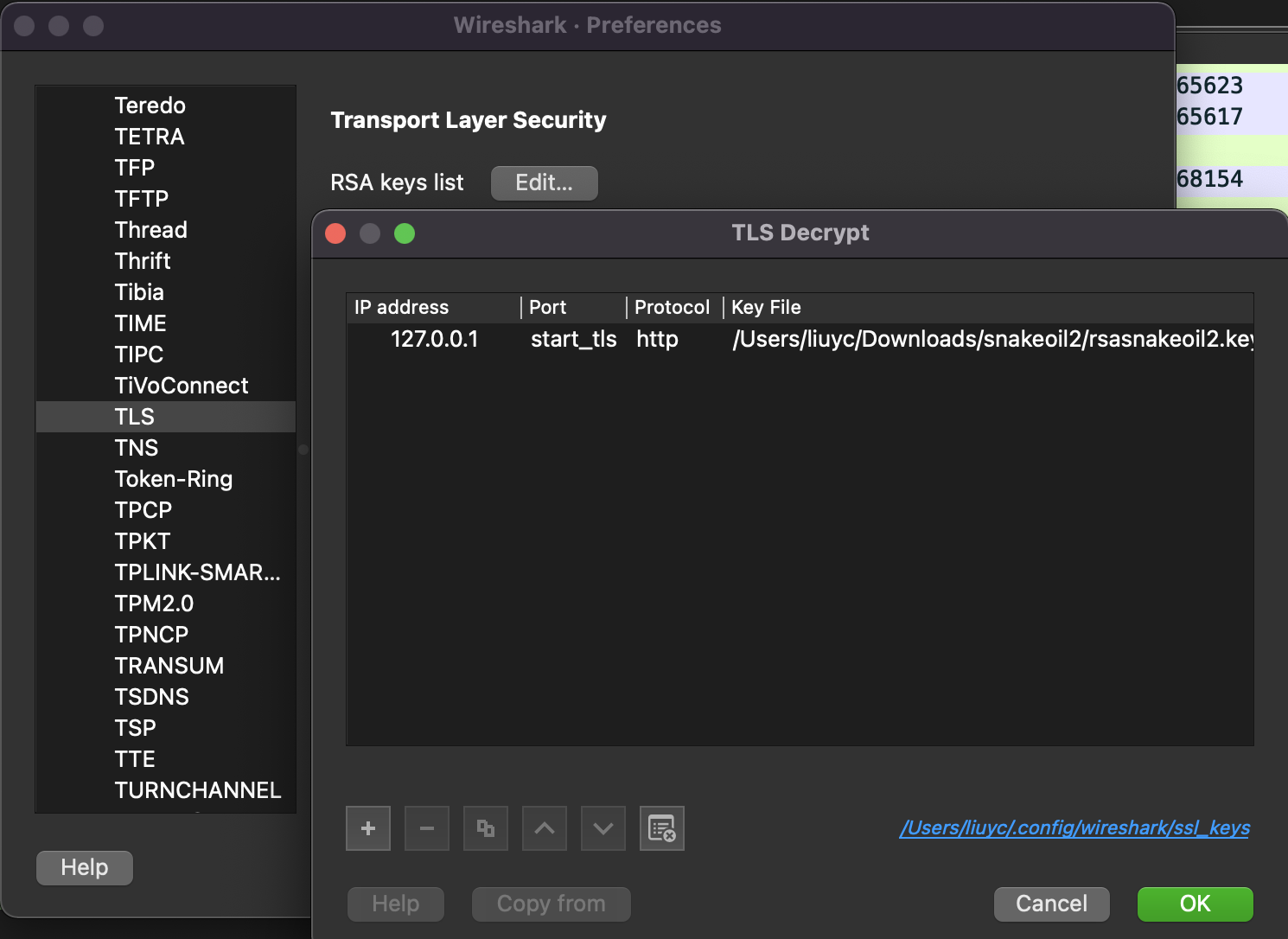
ref:
